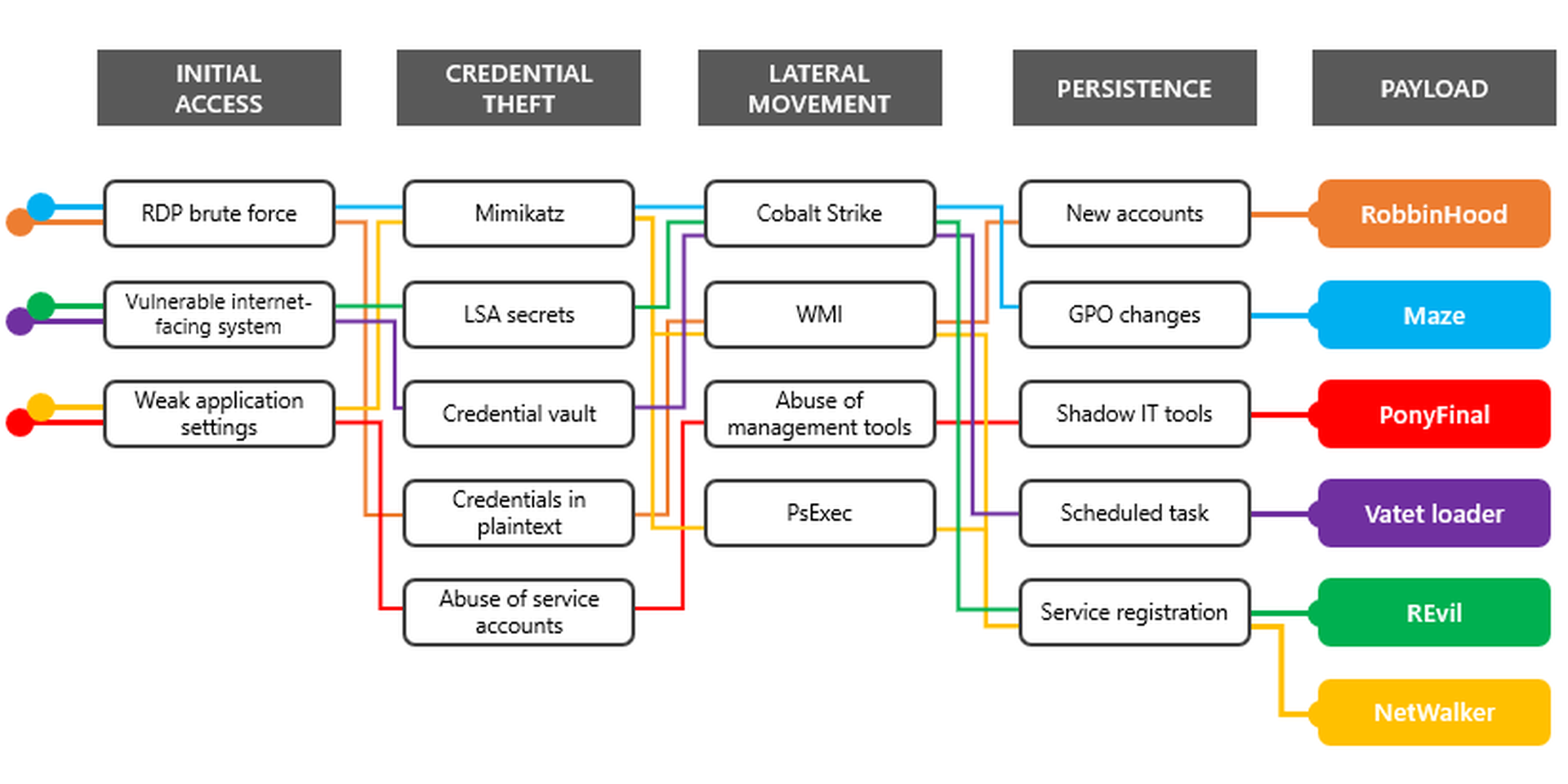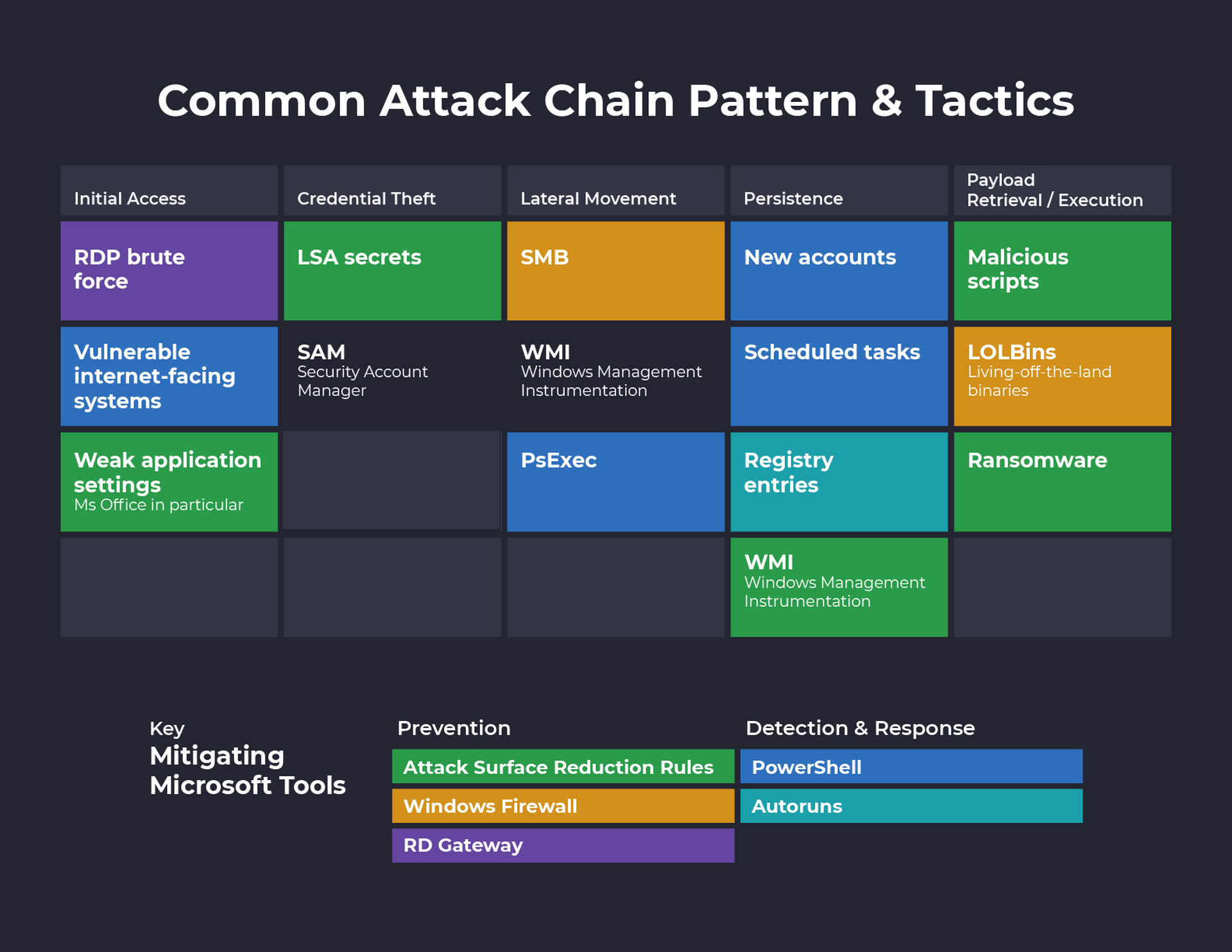
Improving defenses by mapping tools to attack chains
Let’s look at a diagram that the Microsoft 365 Defender Intelligence Team put together in late April 2020. This graphic does a good job of providing a high level overview of what researchers consider to be hallmark post-compromise activities — credential theft, lateral movement, and persistence — bookended by the parts many non-security experts focus on most — initial access and payload execution.