With client-wide infections being reported on a weekly basis, MSPs need to balance prevention with response planning, so when the worst happens, they’ll be ready.
 Author: Jonathan Crowe, Director of Content & Brand Strategy at NinjaRMM
Author: Jonathan Crowe, Director of Content & Brand Strategy at NinjaRMM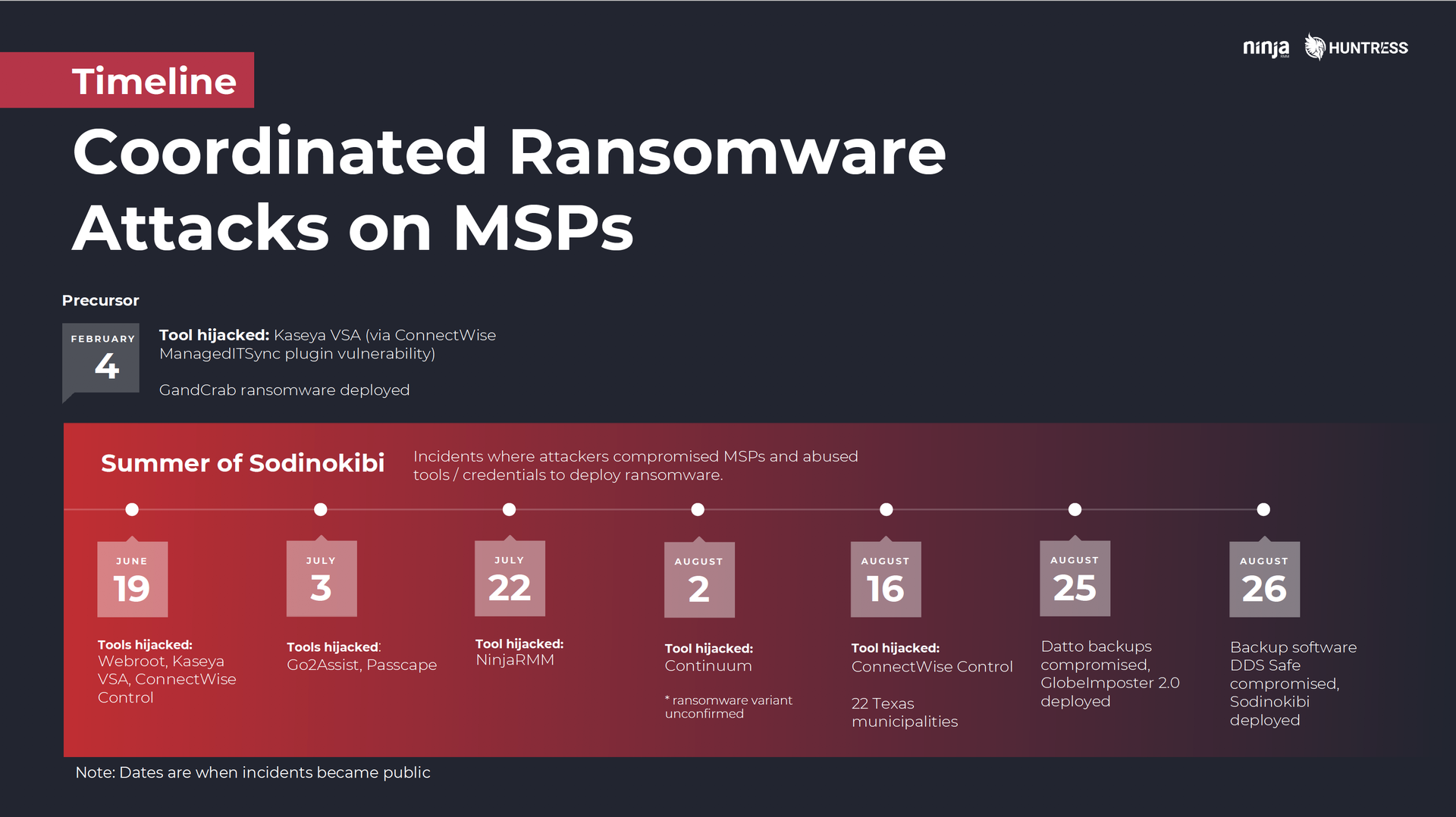
Note: If you’re using RMM or remote access software and you haven’t setup 2FA, stop reading and do that now. It’s truly not a matter of if you’ll see one of these attacks, but when.
While we’re talking prevention, here are two additional recommendations that are super basic, yet incredibly effective. In fact, they can help keep you safe from the majority of today’s most common ransomware attacks:Two Reasons You May Not Be Ready
One of the big things to understand about these attacks is that they aren’t like others you may have prepared for. They’re an entirely different class, with a different scope and different implications. Even if you have well-documented procedures for helping your clients deal with ransomware incidents, those are only going to be, at best, partially applicable here.Why? Two reasons:1) It’s not them, it’s you
Unlike previous incidents, these ransomware attacks aren’t originating in isolation on one of your client networks. They’re being launched from inside your organization. That means you have to have an entirely different set of procedures designed to lock down your own tools and techs until you can identify, isolate, and contain that compromise. Otherwise, if you launch right into trying to remediate client systems, attackers may simply encrypt them all over again until cut off their access at the source.2) Everything hits at once
Here’s another point Kyle made during the webinar that really resonated with folks:You can likely handle one of your clients getting infected. What you likely can’t handle is ALL your clients getting infected at once.
One of the things that has made these attacks particularly devastating for MSPs is the scale. Imagine how stressful and chaotic it can be dealing with one customer infected with ransomware. Now imagine that x 10, 20, 50, or 100. Even larger MSPs can be easily inundated and overwhelmed by the sheer volume of emails and phone calls they have to respond to, the number of systems they have to clean, the amount backups (god-willing) they have to restore.For many, like the small husband-and-wife-run shop PM Consultants, it can all be too much. As detailed in this piece from ProPublica, in the midst of a ransomware outbreak PM announced to its clients via email that it would be closing.The company said it had been “inundated with calls” on the morning of the ransomware attack, “and we immediately started investigating and trying to restore data. Throughout the next several days and into the weekend, we worked around the clock on recovery efforts…. However, it was soon apparent the number of PCs that needed restoration was too large for our small team to complete in any reasonable time frame.”“Receiving hundreds of calls, emails, and texts to which we were unable to respond,” PM ultimately had to throw in the towel, advising customers, “At this time, we must recommend you seek outside technical assistance with the recovery of your data.”
1) Be ready to lock down your own tools
If you have more than one customer notifying you of a ransomware infection at the same time that’s unfortunately a big warning sign you’re dealing with one of these attacks. The first thing you need to confirm or rule out is whether your own infrastructure has been compromised and your RMM and/or remote access tools are actively being hijacked.2) Divide and conquer
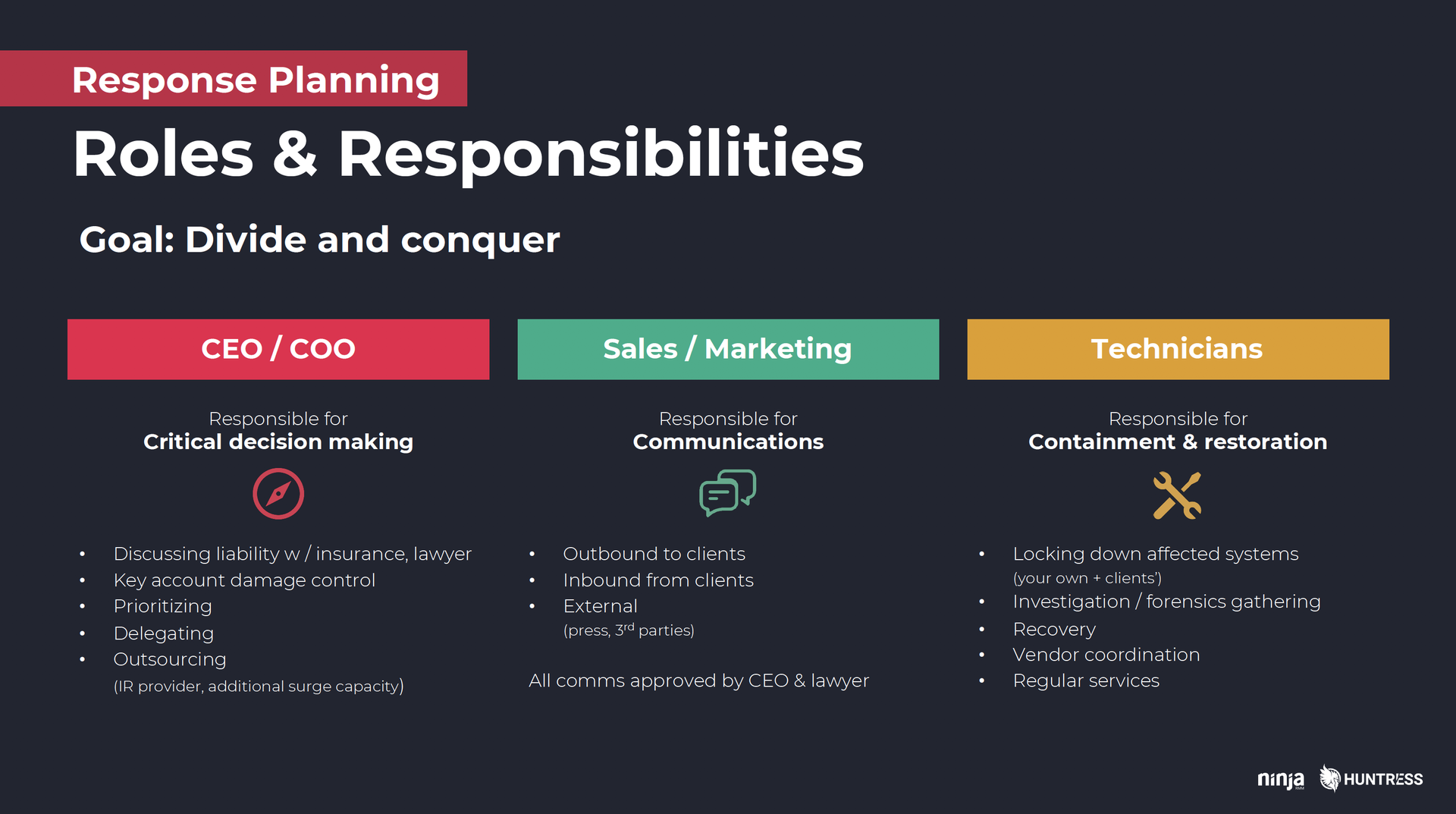
Major responsibility #1: Critical decision making
Owner: CEOSetting the course in terms of:
Major responsibility #2: Communications
Owner: Sales and marketing team, or, if none, CEO and other non-technical staffThe second key need during a live incident is communications. As soon as ransomware hits your affected clients are going to need to know you’re aware of the situation and you’re actively working on it. Otherwise, if they feel like you’re ignoring them or that you’re not in control of the situation, they’re going to panic. They may even to try to assert control, themselves. That’s when things can quickly go from bad to worse and when lawyers can start really getting involved.To prevent all that from snowballing, you need to have people on your team dedicated to establishing and maintaining clear communication channels. That includes:Major responsibility #3: Containment & restoration
Owner: Lead technicianLast but certainly not least, the third major responsibility you need to assign is obviously stopping the attack and getting your clients back up and running. That starts with locking down your own accounts and tools, then locking down affected clients, as well. The initial goal is to stop the bleeding and ensure the attack is contained before diving into active restoration. In fact, it’s strongly advised to engage with an incident response specialist immediately following initial containment efforts (more on that below).In addition to isolation and backup recovery, there’s also forensics gathering and other investigation activities to consider. Depending on how many infected clients you’re dealing with, you’ll likely want to divide these tasks up among your techs. On top of that, you may also have clients that haven’t been affected, but who still need usual support. If everyone has a clear understanding of who’s responsible for what heading into a ransomware situation, the team will be able to move much more quickly and effectively when it counts.3) Develop SOPs
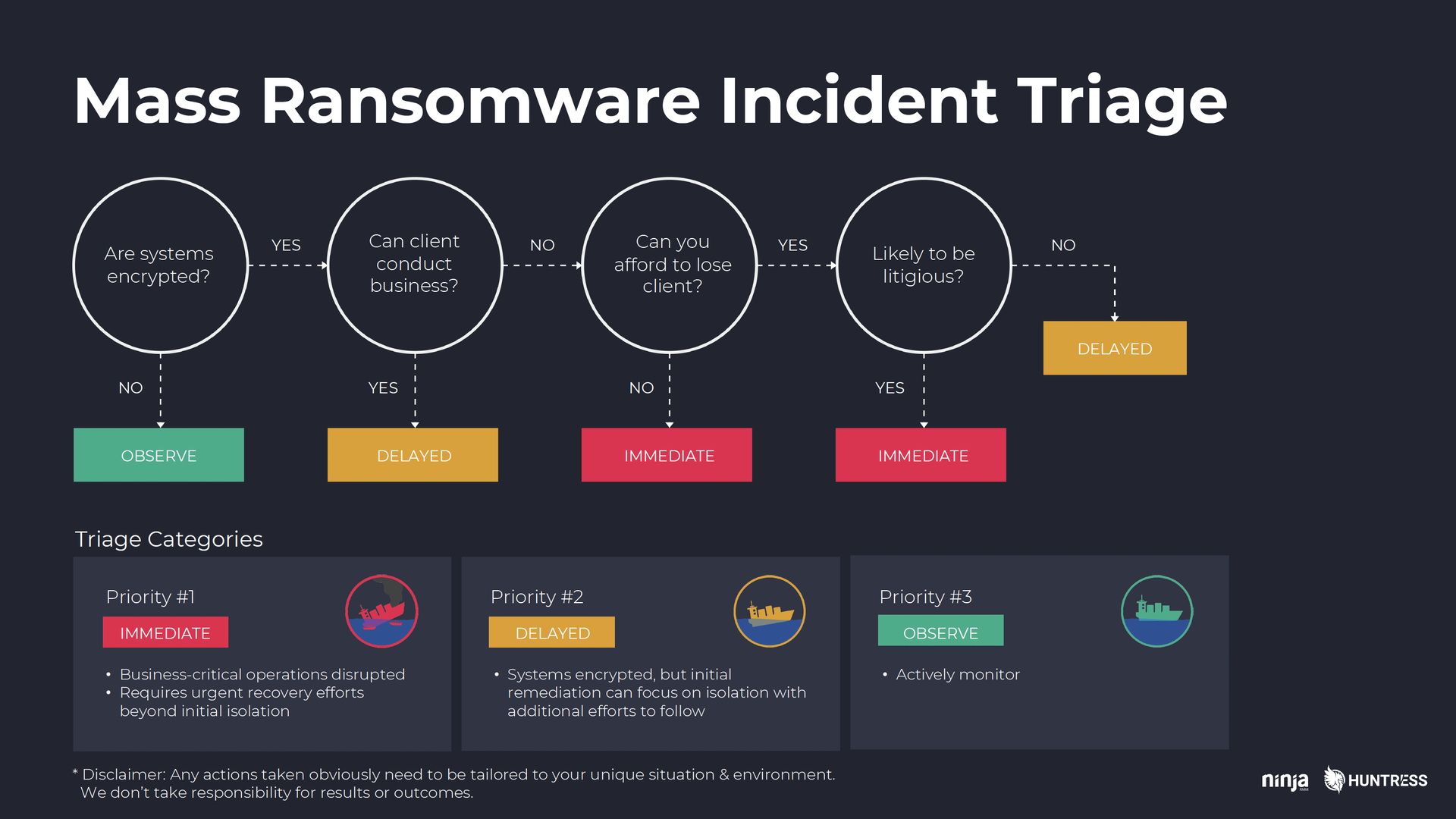
Knowing who’s responsible for what is half the battle. The other half is knowing step-by-step what those responsibilities actually dictate you do. To act quickly in the middle of a ransomware $#*% storm everyone on your team needs to have standard operating procedures they can immediately turn to that remove as much of the guesswork for them as possible.Some extremely basic rules for SOPs:4) Be ready to triage
As Kyle explains, one of the hardest parts of responding to a client ransomware outbreak is the fact that, in most cases, you can’t help everyone at once. As difficult as it may be or as callous as it may sound, you initially have to prioritize some clients over others. To do that, you’ll need a system of assessing need and other factors to determine who gets your attention first.Kyle compares it to the triage training he received in the military (with obvious differences).The chart below was modeled after START, a system developed to guide medical triage in mass casualty situations. There may be different questions or a different flow that’s more appropriate for you and your clients. The point is, determining how exactly you’ll handle client triage is something you need to be thinking about.